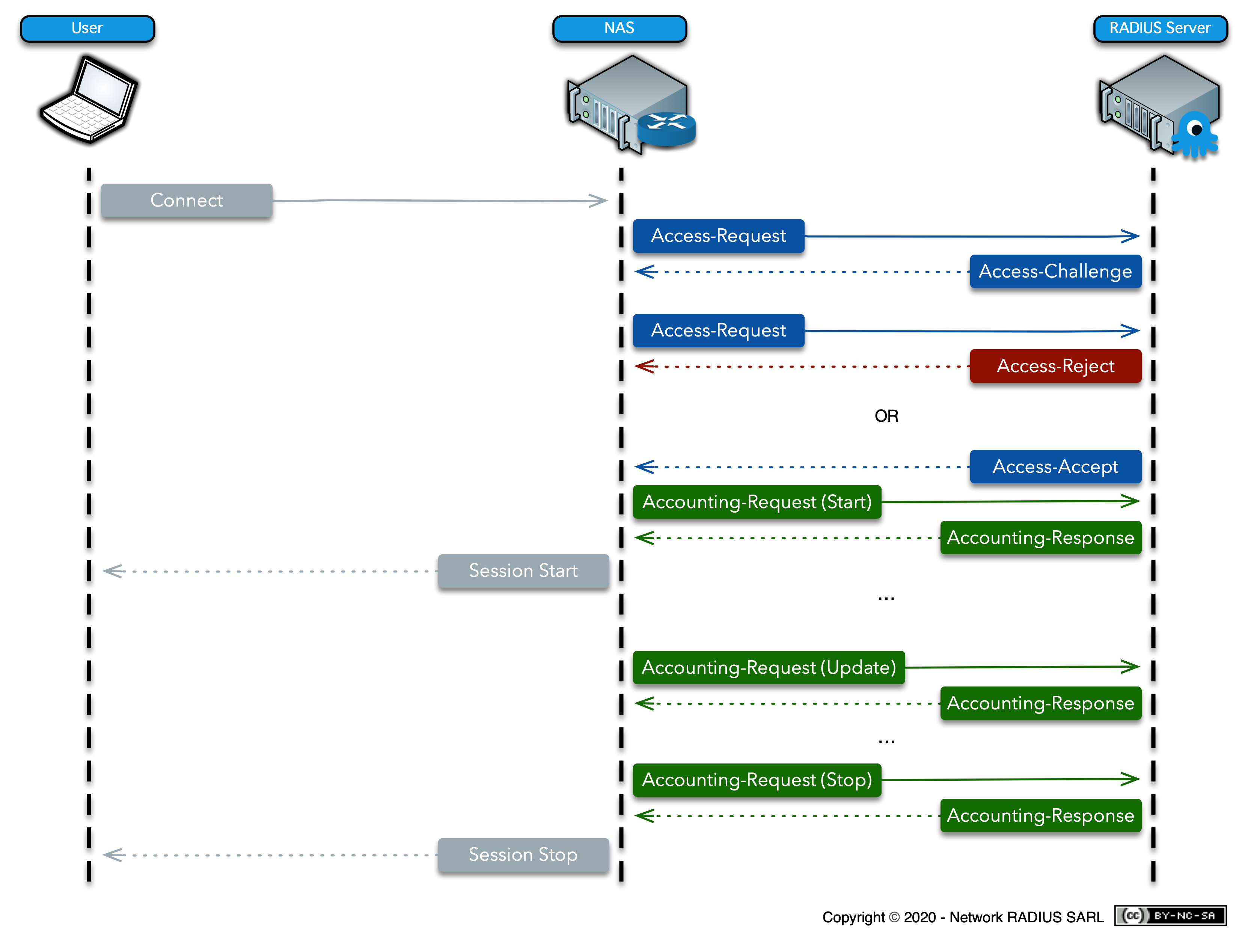
RADIUS authentication starts when the user requests access to a network resource through the Remote Access Server (RAS). The user submits a username and a password, which are encrypted by the RADIUS server before being sent through the authentication process. The request may also include additional user information, such as location or network address.
The RADIUS server then checks the accuracy of the information sent by the user. The RADIUS server employs authentication schemes to verify the data, either checking the user-provided information against a locally stored file database or referring to external sources such as Active Directory servers.
The RADIUS server may respond in one of three ways:
-
Access Accept means the user is granted access to the RADIUS server. Each individual user may be granted restricted access without affecting other users.
-
Access Challenge means that the RADIUS server will request additional information from the user to further verify the user ID. This additional information may be in the form of a PIN, a secondary password, or a card.
-
Access Reject means that the user is unconditionally denied all access to the RADIUS protocol.